Cyber incidents for 2017 show Ransomware affect
In 2017, the ICO changed the way cyber incidents were reported to a more relevant format.
Reporting on the last six months of published cyber incidents, the ICO has changed its reporting format. Instead of telling us what happened – e.g. exfiltration, the focus has shifted to the cause. This is great news for businesses wanting to understand where their risks lie.
Malware and phishing combined make up 39% of all cyber incidents. This includes 12% from ransomware which is a new entrant. This figure will be likely to increase with the likely spread of Meltdown and Spectre style attacks. There are potentially billions of un-patched devices which will remain in circulation over the coming years.
File-less attacks have also been reported to be on the rise. These leveraging valid system tools such as PowerShell, these attacks are harder to spot.
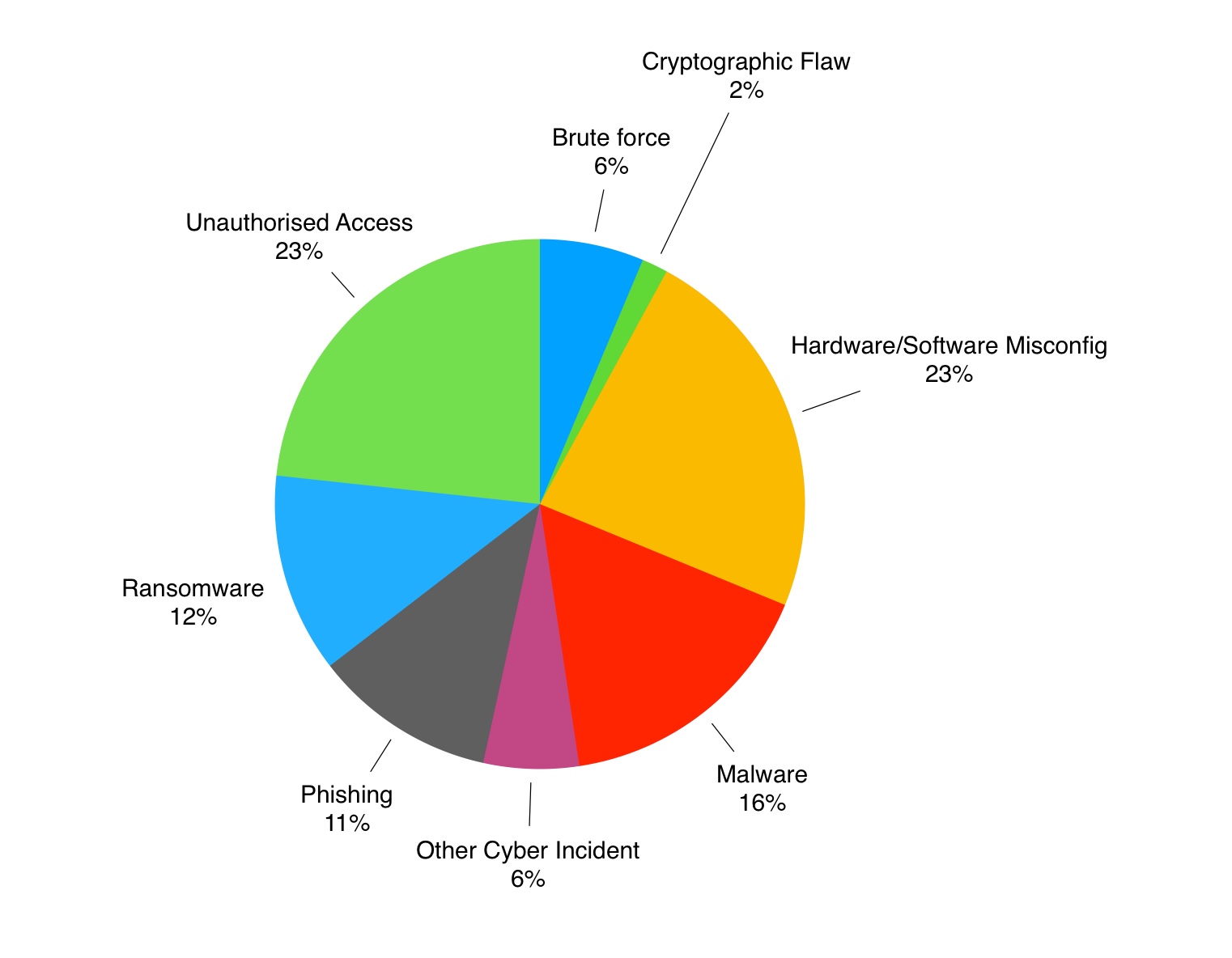
Misconfiguration
Hardware and Software misconfiguration represented nearly a quarter of all reported cyber incidents in the six months to September 2017 – and should be a learning point for all businesses. Cyber risk can never be prevented – only managed – but hardware and software misconfiguration is a preventable situation.
Brute Force
Brute force attacks against susceptible accounts are also inexcusable. We know from running cloud environments and honeypots that well known ports such as SSH, SQL and RDP are magnets for brute force attacks. Software such as WordPress is also susceptible out of the box as there is no password lockout facility in the standard build of the product.
Multi-factor authentication and password lockout should be made standard practice. With only a few exceptions, they can provide solid protection for your most valuable data. We’d pass at the ‘Butt scan’, though!
Bringing the phishing risk down
Sorry to say this, but there is no easy cure for phishing. You can train people until you are blue in the face – the whole reason phishing works is that it’s a form of social engineering.
Sales departments are at the highest risk of responding to a phishing attack – but the second highest is… the IT department!
Reducing phishing requires some joined-up thinking:
- Break phishing down into its four main types
- Tackle each type separately with processes and/or technology e.g. malware dropping requires good endpoint protection
- Train users not to avoid links (because they can’t) but instead to report click-throughs
Posted
13th January 2018
(7 years ago) under