Business Gateway publishes bad cyber security advice
Scotland's business support network Business Gateway recommends "changing passwords regularly" - advice which was discredited in back in 2015.
I was pleasantly surprised to see a piece in the local newspaper promoting cyber security workshops. Offered by Business Gateway – Scotland’s business support network, it was sadly a missed opportunity – giving out advice that was outdated and potentially dangerous.

“Changing your password regularly is also important”
Some ideas are great when you first think of them – but unfortunately they don’t stand the test of time. Password changing is one good example.
CESG (now NCSC) debunked this myth three years ago and countless others have said what every IT manager has known for over 20 years: asking people to change passwords on a regular basis has no particular security benefit – all it does is encourage the use of weaker and weaker passwords. Password12 today becomes Password13 next month. Anything more complicated than that and it ends up on a post-it note stuck to the monitor. It’ll probably end up on a post-it note anyway because Jane from accounts or Suzie at the till needs to know it.
“Three, Four, Five, Six…”
There then follows some very uncertain advice about password creation. This goes against the UK Government’s much clearer message. Just. Three. Words. Simple as that.
Hang on, I hear you say. Three words are rubbish against combinator attacks – and you’d be right. There might be 171,000 words in the English dictionary – but most of us rarely use more than 20,000. And when asked to think of a password using three words – I’d put money on at least two of them being a high frequency word – perhaps one in a thousand. 1000 ^ 3 becomes a just one billion combinations – and if I fire up an Azure or Amazon cloud I can probably attempt 200 billion password combinations against an MD5 hash every second. My three word password will last no more than a blink of an eye.
But that’s not the issue. You see, it’s all about pragmatism. Three words are easy to remember – certainly they’re better than coming up with passwords that have traditionally been tough for people to remember but easy for computers to break. If you also advise people to use different passwords for different systems – a combinator attack against a stolen hashed user database becomes moot because the cracked password is useless against a different network. No-one is going to use a password to access an account on a system they’ve already broken into!
Stick to three words. The result is so much easier and clearer – and it stops forcing people down the road of the top 25 passwords used by 10% of the English speaking world… The takeaway, however isn’t the choice of password at all – the takeaway should be to use a different password for different accounts – or (at the very least) not share your most important logins with your knitting or car forums.
Back to the matter in hand: Business Gateway are recommending “three or four” – but then they add these passwords should also include some numbers as well “to make it harder to guess”. (There is no mention of symbols being used, which is in the published government guidelines). The reason numbers and symbols are mentioned in the guidelines, of course, is that they’re often a requirement for some accounts. They are not a requirement for a strong password.
The clue is in the wording – “harder to guess”. This is written by someone who clearly doesn’t understand how passwords are actually stolen. Passwords aren’t guessed on any great scale – they’re brute forced against tables of hashes. If the hash is weak such as MD5 – then happy days – there are lots of options. For many hash types, rainbow tables are available which speed up the process – especially if the hash isn’t SALTed. I come back to the flaw in Business Gateway’s argument: no-one is going to use a password to access an account on a system they’ve already broken into!
What you should really do…
Because of the way passwords are actually compromised – the best approach (which again, was never mentioned in the article) is to reduce password dependency. Changing passwords only when compromised and instead leveraging Single Sign-On (SSO) – which anyone with a Facebook or Gmail account can do, backed up by 2FA – which only 10% of Google users actually turn on. Finally – using separate passwords for your important accounts is a must.
Which brings me to my next bugbear…
“Use a password manager… which adds another layer of security”
No it doesn’t! Aside from the fact that password managers are a necessary evil, they don’t actually add a “layer” of security*. Yes, there are some side benefits in that you don’t have to remember your machine-generated password even if you use multiple devices – but then you also have to factor in what happens when you leave your device unlocked with the kids / ex-husband / evil maid – who then potentially gets access to your entire life.
Using Two-Factor Authentication (Google Authenticator or even better – a hardware U2F key like FIDO) is a good example of adding another layer of security. This ensures that even if your password is compromised, no-one else is getting access to your account.
Phishing emails having “odd sender addresses” and “full of spelling mistakes”
It’s 2018 and many computers now have spell-check built in! Aside from the daughter of the ousted former ex president of Nigeria who just wants to bring $200,000,000,000,000 in gold and diamonds into the country and can she have your bank details please – phishing has come of age.
I defy people to tell the difference between a genuine e-mail and a correctly curated phishing e-mail – such as the examples below. In case you were wondering – neither could around 80% of the IT staff the phishing e-mails (the ones on the right) were sent to.
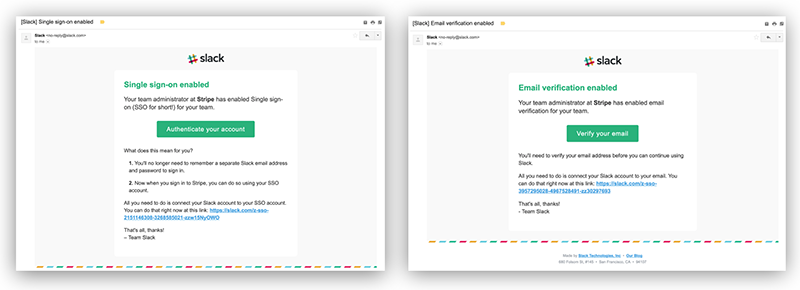
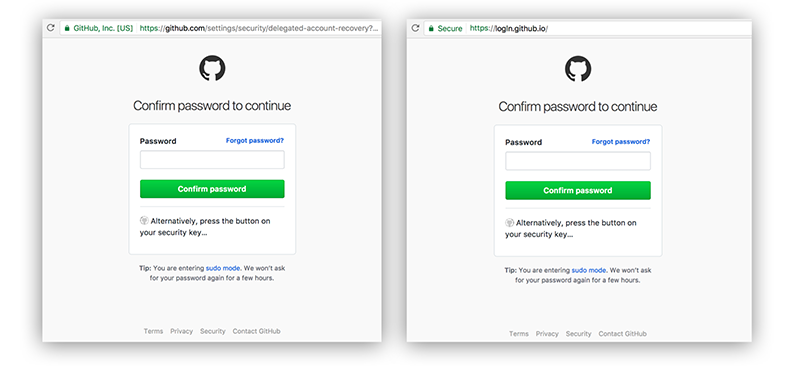
Don’t click on the links…
The trouble is – everybody does click on the links. It doesn’t matter how much you spend trying to show people how to spot a phishing e-mail (a) they can’t and (b) they won’t. Case in point, most research shows that Execs and IT staff are the two groups most likely to fall for phishing attacks – these are obviously the people that should know better, but ironically they are also the people with the most power inside an organisation.
In a great paper entitled “Ichthyology – Phishing as a Science” presented at Black Hat 17, Karla Burnett of web-payments engine Stripe completely debunked the notion that people can be educated to not to click on the links. The reason is the paradigm of fast and slow thinking – first proposed by Daniel Kahneman. In short: the human brain is reading through your inbox instinctively – and reacting just like it would when driving a car. We’re not processing the information in front of us – it would take far too long – so even if the e-mail was full of typos, you will click on that link. Or to put it in the words of the NCSC – trying to stop phishing just wastes your organisation’s time and money.
The only strategies around phishing are ones which accept that people will click on the links. Harden the endpoints to reduce the potential damage – install damn good endpoint protection – and make it clear what people should and shouldn’t do when they realise they may have clicked something they shouldn’t.
Be careful giving people cyber security advice!
Giving advice is easy – giving good advice is a skill.
I myself started writing advice on IT security for magazines both on- and off-line back in 2003 – and even fifteen years on, deciding what to say can sometimes be a challenge. There’s usually a great deal of procrastination and a lot of scribbling – the NCSC has summed the process up really rather well.
The trouble is you don’t know who will read your article – their own situation and experience may be different to what you expect. Which is why everything we include in our advice be it for online magazines, our blogs or or our own training courses – is heavily researched.
We check and cross-check our advice to make sure it tallies with the very latest cyber security thinking. We check over fifty different industry sources – often bouncing our ideas off colleagues to check our assumptions. Only then does advice get committed to print.
How did Business Gateway get it so wrong?
We’ve previously been advised by Business Gateway that cyber security was something they had “covered” – something which had been previously put out to tender. Having worked with several large training companies and colleges – we know the darker side of the training industry.
The subject matter experts who win the tenders aren’t generally the people delivering the courses. Sometimes, quite often in fact, they aren’t even involved in writing the courses. I’ll go a stage further and suggest that sometimes the courses aren’t even written but… simply bought in.
Perhaps something that’s been on the shelf for a while but still serves them well.
The problem is the training industry is built around scale – rack ’em high and sell ’em cheap. You can’t have subject matter experts delivering courses – you get your team in Manchester or Mumbai working on a new course – then you sell the same course for four years (the life cycle of an operating system).
We have some clues – one of the quotes is that a Scottish hairdressing business was attacked in 2015. Given the large number of up to date small business attacks that are published (for one source, go check out the Information Commissioner’s website at the moment) – one can assume that the information in the press article comes direct from the course. A course written in 2015 perhaps – around the time that CESG was announcing its new recommendations for password security?
The trouble is – security isn’t a Microsoft operating system. It’s changing daily – and if businesses want the best advice, a three year old course regurgitated by a contract trainer who’s never played for the red team isn’t going to cut the mustard. Let’s take another example…
Software updates
In the article, we are told “making sure all your software is up to date is vital”. True enough – but this went to press at the end of January 2018 – a month where the most significant vulnerabilities ever discovered in the history of computing came to light. Why is this important? It’s important because the vulnerabilities of Spectre and Meltdown require firmware updates – and for instances where no firmware updates exist comes the real prospect of having to relegate unsupported equipment to the bin.
This wasn’t the only problem with hardware in January. Multiple vulnerabilities were uncovered in IoT and other network devices including Western Digital drives – the kind of boxes people buy in Asda or PC World to back up their computers. Essentially anyone on the Internet using the hard-coded password “mydlinkBRionyg” can connect to the device and control all of your data.
Telling people to simply update their software is not enough. They need to understand that every application they have, every device they have, and every piece of hardware – from backup drives to tills – may need updating. And for the devices that can’t be updated, the bin awaits.
More of the same…
I won’t dwell on the other deficiencies in the article. One hopes that I’m completely wrong and that the actual content of the workshops on offer is sound – and that the people delivering it are not simply contract trainers with no actual CTF experience. That, I’m afraid, really would be criminal.
All you need to know is that our courses are bang up to date – and do feature the latest thinking from the National Cyber Security Centre and top industry sources. That way you’ll be getting the very best advice.
* To be absolutely fair: there is one small exception and that is when credentials are being phished – password managers can help spot a fake website but only by virtue of not recognising a similar looking but different website and not populating the password form – but that’s a byproduct and it’s not a thing. There are ways around this – and we’ve tested a number of password managers out in different scenarios and it is possible to get them to leak passwords on certain websites – defeating the whole point.
Posted
2nd February 2018
(7 years ago) under